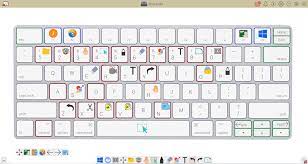
Windows 11 keyboard shortcuts make it easier to navigate your PC without reaching for the mouse. These handy key combinations allow you to zip through tasks and access features that might otherwise be buried in menus. There are dozens of Windows shortcuts available, but there is a subset that I...
RevITup TechBytes Technology Blog
Update Your Chrome Browser Now! Zero-Day Exploit Found
As reported by the information security blog Bleeping Computer, Microsoft researchers identified a critical vulnerability in the Chrome browser that requires immediate attention. This security flaw is a zero-day exploit that is already actively being used by hackers to attempt unauthorized access into computers through the Chrome browser. So while...
Microsoft Office Apps Provide a New Path for Hackers
Microsoft has disclosed a zero-day "max severity" vulnerability that impacts several Office and 356 products. Attackers may exploit this vulnerability to steal private data from individuals or organizations. A patch was made available on August 13th. The flaw in question, nicknamed "Microsoft Office Spoofing Vulnerability" and tracked as CVE-2024-38200, is...
Hackers Are Using Google Search Ads to Impersonate Google
Phishing links and malware are a familiar threat to anyone who browses the internet. Still, sophisticated attacks can catch even the most security-minded users off guard. And nothing's more sophisticated than impersonating Google on Google's own platform. In a recent malicious advertising campaign, hackers purchased "Sponsored" Google Search ad space...
How to Get Better WiFi
If you work from home or follow a hybrid work schedule, chances are you've been confronted with slow internet connection speeds, especially now that the kids are home from school. There are two main reasons why your WiFi could be slow: your ISP isn't delivering a speedy connection to the...